Examples of phishing attacks and how they work
All data – from email addresses and passwords to financial data or even a person’s address – is valuable to a hacker. Any item of personal data provides information essential to commit fraud.
Every day 3.2 billion people send around 269 billion emails.
Researchers at Symantec suggest that almost one in 2,000 of these are a phishing scam. Often people rush through their inbox without analysing every message that lands there – making room for cyber threats.
Knowing how to spot a phishing email is one way to lower risk. We give examples of phishing emails in the article below and give detail on how you can protect your organisation.
What is a phishing scam?
Phishing scams are one of the simplest ways for a cybercriminal to attack a business, though it is one which can provide the criminal with everything they need to infiltrate every aspect of their target.
A phishing scam normally takes the form of an email, though the technique has now started to spread into social media, apps, and messaging services.
The scam tries to trick the target into doing what the hacker wants.
That might be handing over passwords to make it easier to hack a company or altering bank details so that payments go to fraudsters instead of the correct account.
Phishing attacks on the rise
In a recent article, we have discussed how phishing attacks are increasing. Proofpoint’s 2019 State of the Phish Report revealed that 83% of survey respondents experienced phishing attacks in 2018, a whopping increase of 76% from 2017. Phishing is a persistent threat to businesses, and it is crucial to know what phishing attacks are and what damage they can do to put the appropriate barriers in place.
Here are five reasons why phishing attacks are on the rise, so you can stay in the know with cyber security.
1. Users are easy to trick
Computer and electronic users are just ordinary people, and most of us are not trained to recognise phishing attacks. We often fall prey to cyber attackers’ tricks, mainly because their communications can be uncannily like those of the organisation they are trying to impersonate. One click of a false web link or a false attachment in an email can cause serious damage.
Simply being able to identify what a phishing attack looks like will help prevent many people from falling for one in the future.
2. Malware is becoming more sophisticated
Malware and ransomware are constantly evolving, and this type of attack can present itself in several ways. A single security solution may not be sufficient to defend against all security attacks, which is why it is essential to frequently review your organisation’s security strategy to ensure it is working as well as it can be. As the cyber security landscape develops, one of the best and easiest ways to protect your organisation against attacks is to update your software automatically. With new updates come the latest bug fixes, effectively filling in possible gaps in your cyber defences.
3. Phishing tools cost barely anything
There are a lot of tools out there which teach amateurs how to launch phishing attacks of their own. These are called phishing kits and it is easy for anyone to get their hands on one. This means that phishing attacks are becoming more widespread around the world, leading to greater potential damage to organisations.
4. Organisations often do not have security barriers in place
Many organisations do not have a cyber security strategy, which makes them easy targets for phishing attacks. There are tremendous financial and reputational risks for businesses that are successfully attacked. It is in the best interests of all businesses to do more to protect themselves from cyber attacks. Cyber Essentials is a great first step to take which will protect your organisation from 80% of the most common cyber attacks, including phishing.
5. COVID-19
Deloitte’s Cyber Intelligence Centre has observed a spike in phishing attacks, Malspams and ransomware attacks as attackers are using COVID-19 as bait to impersonate brands, thereby misleading employees and customers.
Deloitte has reported that:
“Not only are businesses being targeted, end users who download COVID-19 related applications are also being tricked into downloading ransomware disguised as legitimate applications.”
How do phishing scams work?
Phishing scams vary in their mechanics.
Phishing attacks, sometimes referred to as spear-phishing attacks, attempt to gain sensitive, confidential information from users by pretending to be communications from a legitimate person or institution. They come in the form of text messages, emails, phone calls or whole websites and present in the same form as the legitimate organisation they are impersonating. Attackers hijack information from authentic organisations to create highly customised emails, making them appear entirely realistic and credible.
Some promote links to a fake website with the aim of persuading victims to enter personal information whilst others involve tricking users into downloading and installing malware. The latter can result in ransomware, which ultimately leads to immediate profit for the hacker.
However, not all phishing scams are as simple as this. More complex scams can take place over months or even years where selected individuals are targeted for specific data. In these cases, the hacker uses fake social media profiles and emails and builds up a rapport with the victim.
Phishing attacks in action
Phishing hackers will often use a big brand as their disguise when infiltrating your email address. PayPal is often mimicked by hackers. This example from WeLiveSecurity shows a well-executed scam.
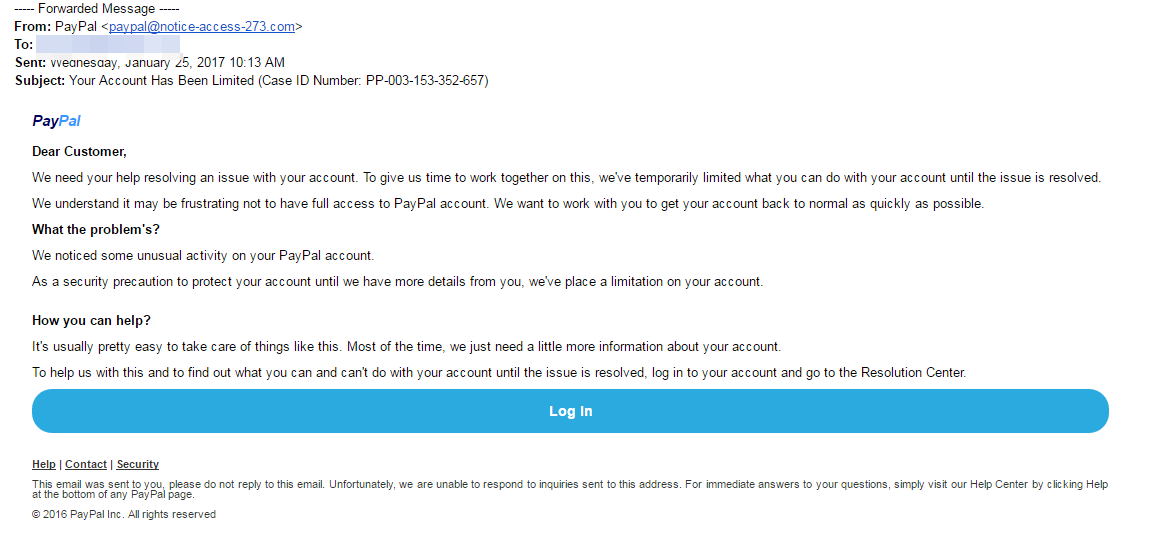
Not only does the email contain PayPal’s official logo at the top of the message, but it is also styled professionally, and the request is believable.
That said, there is one huge red flag: the sender’s email address, ‘paypal@notice-access-273.com’.
Always look at the sender’s email address as a genuine email will usually include the organisation’s name in the domain name. If the domain name matches the apparent sender of the email, the message is most likely legitimate.
Although this is common knowledge, in some cases this may be enough to trick the recipient as a glance at the word PayPal in the email address, together with the smooth layout could be enough to satisfy them that it is genuine.
Watch out for misspelt domain names
A misspelt domain name is a prime example of how you can spot a phishing email.
As anyone can buy a domain name from a registrar, this is one way hackers can trick their victims into thinking they are a legitimate organisation.
Some hackers will use slight misspellings to trick the recipients into thinking they are organisations like banks, credit card companies etc, this is known as “typosquatting”.
NBC News has reported on this trend in recent years, due to the rise of this phishing method. NBC reporter Herb Weisbaum warned that hackers are reliant on human error:
“Scammers are counting on your typos — and are ready to pounce if you slip up when entering a web address into your browser. Just one wrong keystroke could send you to a typosquatter’s look-alike site that can install malware, steal sensitive personal and financial information, or even lock up your computer.”
And don’t assume that an incorrect URL will result in an error message — because that’s the evil genius of typosquatting. Since these malicious sites are registered, your browser doesn’t see the typo as an error, so it makes the connection.”
Famous phishing email example: Operation Phish Phry
One of the most famous phishing attacks in history was Operation Phish Phry.
This famous cyber attack affected hundreds of bank and credit card customers, as they received official-looking emails directing them towards fake financial websites.
The attack fooled many of the recipients as the victims entered their account numbers and passwords into fraudulent forms, which gave cyber criminals easy access to their private data.
The cyber crime which took place in 2007 was relatively simple by today’s standards, but extremely effective. Those behind the attack managed to steal about $1.5 million from hundreds or even thousands of bank accounts.
This famous phishing attack led to a multinational investigation conducted in the United States and Egypt. Forbes has since reported that “operation Phish Phry resulted in 53 defendants being named in a 51-count federal indictment, and 47 suspects being charged in an Egyptian court.”
What can you do to protect yourself?
The National Cyber Security Centre (NCSC) recommends a multi-layered strategy when fighting phishing attacks:
“Typical defences against phishing often rely exclusively on users being able to spot phishing emails. This approach will only have limited success. Instead, you should widen your defences to include more technical measures. This will improve your resilience against phishing attacks without disrupting the productivity of your users.”
Cyber Essentials Online recommends the following steps:
1. Don’t click links on emails.
Emails can become hijacked and accounts can be replicated to fool a potential victim.
2. Bookmark your favourite sites
You will be able to go directly to the sites that you trust and reduce the risk of being spoofed via a link or typo. If you receive an email from a company telling you to contact them, do not click on a link but go via their website to find authentic contact details.
3. If you are an employer, support your employees
It is important you and your staff are aware of threats. Training is vital, as it will support the detection of phishing on the frontline. As an employer, it is also your responsibility to create an environment that encourages users to report phishing attempts.
4. Do not underestimate password protection
Passwords are still a key target for phishing attackers. The NCSC has recommended #ThinkRandom for a few years and is still promoting this method of password creation.
Instead of creating extremely long and complex passwords, the NCSC’s #ThinkRandom recommends that, when setting up a password, users choose three random words. Examples used on the NCSC website are: ‘coffeetrainfish’ or ‘walltinshirt’.
Avoid using easy to guess passwords, such as ‘onetwothree’ or the names of family members or pets as this will make you an easy target for hackers.
5. Invest in Cyber Essentials
Cyber Essentials will protect your business from up to 80% of cyber threats and allows you to focus on core business objectives knowing that your business is protected.
You can also increase your chances of securing business by demonstrating your commitment to protecting your own data as well as that of customers and suppliers.
Cyber security is more important than ever before
Get Cyber Essentials Certified
Officially backed by the UK Government, Cyber Essentials is a great solution for businesses looking to improve their cyber security settings and standing. By implementing five simple key controls, you can protect your business from up to 80% of common cyber security threats.
Find out more about our packages and get started with your Cyber Essentials certification.
“I’m already Cyber Essentials certified”
If you would like to retain your Cyber Essentials certification, then you must recertify annually. When your certification is coming to an end, Cyber Essentials Online will inform you by email around 30 days before you are expected to recertify.
Due to the popularity of the Cyber Essentials certification, we recommend that when you receive this email you begin preparation, as this will ensure that your application goes through before your current certification expires.
Remember, if your business has experienced changes to its security infrastructure, your answers should reflect this. If not, keep in mind that your answers should be like those on previous Cyber Essentials questionnaire/s.
